Open up Server Manager and add a new role.
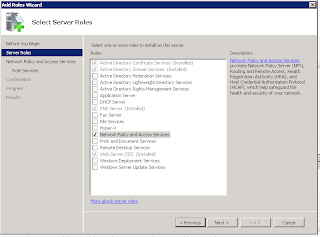
Select Network Policy and Access Services. Click next and you only need to have the Network Policy Server selected to hit next again and install.
After the installation is completed. Open the Network Policy server and expand Policies, Network Policies and create a new network Policy.
Create a name for the Policy and leave the access server to unspecified click next.
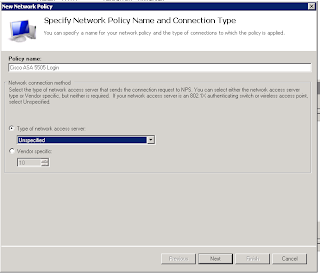
Add some conditions for access like Windows user groups or something
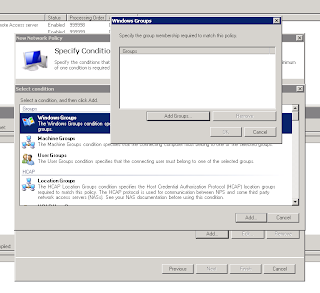
Click add groups and then type in the Group name, I went ahead and added Domain users just for testing. I also added the RADIUS client settings under the condition and specified the name of my ASA
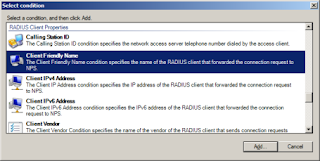
After you are done adding the conditions, click next and select access granted and next again
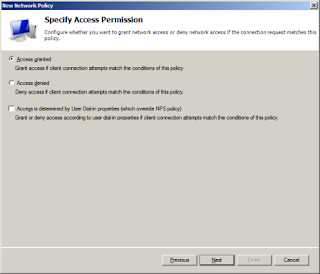
Put a check make on Unencrypted authentication (PAP, SPAP).
Click next, and select No when it ask you to view the help file.
It will ask for setting additional constraints, we don’t need any, click next.
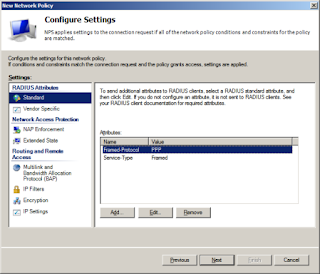
Under standard RADIUS attributes, deleted PPP and Framed and add a new one.
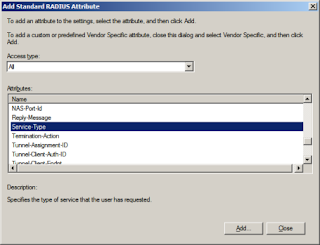
Access type will be all and attribute is service-type
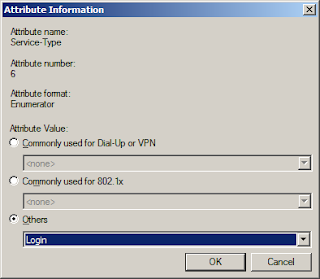
The attribute value will be Others, then choose Login the drop down box and click OK, then Close.
Specify the vendor under RADIUS Attributes by adding select Vendor Specific.
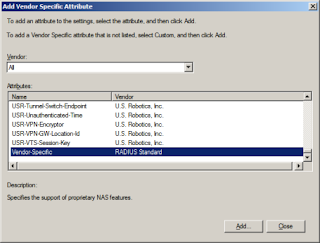
With Vendor set to “All”, select Vendor-Specific for the attribute and click Add to add in the attribute information.
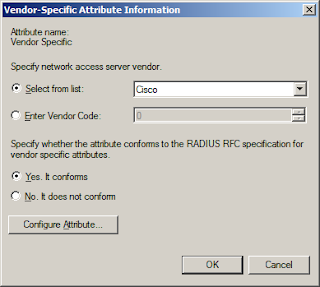
For the attribute information select “Select from list” and choose Cisco from the menu. Then select “Yes. It conforms” and click Configure Attribute.
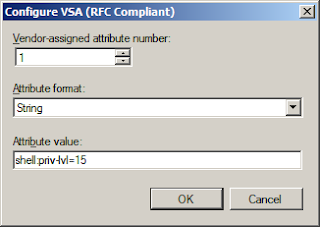
For the Vendor-assigned attribute number enter 1, for Attribute format choose String, and in Attribute value type:
shell:priv-lvl=15
Then click OK.
Click OK, Close, Next, then finally click Finish.
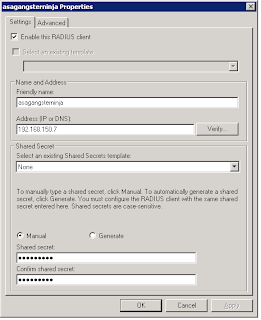
Now specify the Cisco router as a RADIUS client in Network Policy Server by highlighting RADIUS Clients and Servers, and then right click RADIUS Clients and choose New.
Fill in the friendly name that you specified earlier and enter the IP address for the device and enter the shared secret RADIUS key.
Activated in Active Directory. Right click the NPS tree root on the left pane, and choose “Register server in Active Directory”. (If it is shaded out do not worry about it.)
Restart the NPS services which might take a few seconds and then everything should be complete now.
No comments:
Post a Comment